Mobile Malware Attacks And Defense: A Comprehensive Guide To Safeguarding Your Devices

The Ubiquity of Mobile Devices and the Growing Threat of Malware

4.7 out of 5
| Language | : | English |
| File size | : | 5625 KB |
| Text-to-Speech | : | Enabled |
| Enhanced typesetting | : | Enabled |
| Print length | : | 666 pages |
In the modern digital age, mobile devices have become indispensable companions, connecting us to the world at our fingertips. From smartphones to tablets, these devices empower us to communicate, access information, conduct business, and engage in countless other activities. However, the widespread adoption of mobile devices has also inadvertently created an expanded attack surface for malicious actors.
Cybercriminals are constantly devising sophisticated malware attacks to exploit vulnerabilities in mobile operating systems and applications. These attacks can have devastating consequences, ranging from data theft and financial loss to identity fraud and device compromise.
Unveiling the Menacing Techniques of Mobile Malware
1. Phishing Attacks: Luring Victims with Deceptive Emails and Text Messages

Phishing attacks are a common tactic used by cybercriminals to trick users into divulging sensitive information such as passwords, credit card numbers, and personal data. These attacks often involve sending emails or text messages that appear to come from legitimate organizations, such as banks or social media platforms. The messages contain links that lead to偽裝成 legitimate websites, where users are prompted to enter their credentials or other sensitive information.
2. Malicious Apps: Disguised Threats Lurking in App Stores

Malicious apps are another major threat to mobile devices. These apps often masquerade as legitimate and harmless applications, but they contain hidden malicious code that can compromise user data and devices. Cybercriminals may distribute malicious apps through official app stores or third-party sources, making it difficult for users to identify and avoid them.
3. Spyware: Stealthy Infiltrators Monitoring Your Every Move
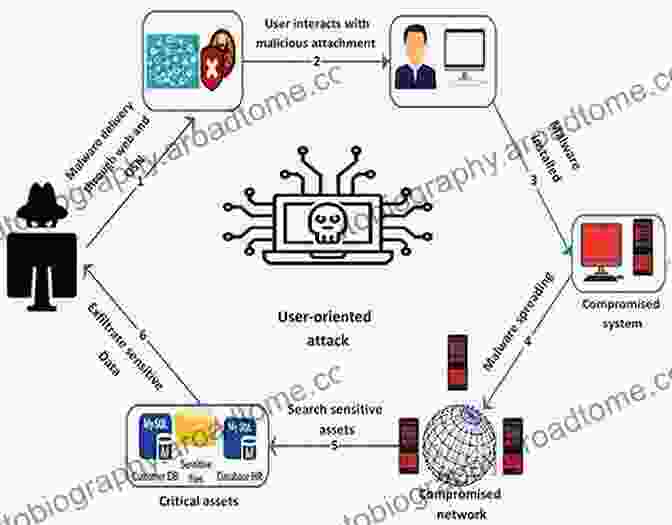
Spyware is a type of malware that can surreptitiously infiltrate mobile devices and collect sensitive information, such as GPS location, call logs, text messages, and even audio recordings. This information can be used for identity theft, financial fraud, or other malicious purposes.
4. Ransomware: Holding Your Data Hostage for a Price

Ransomware attacks encrypt user data and demand a ransom payment in exchange for decrypting it. These attacks can be particularly devastating for mobile devices, as they can render essential data and files inaccessible.
The Devastating Consequences of Mobile Malware Attacks
1. Data Theft: Compromising Your Privacy and Security

Mobile malware can steal a wide range of personal and sensitive data from your device, including passwords, credit card numbers, social security numbers, and more. This information can be used for identity theft, financial fraud, and other crimes.
2. Financial Loss: Draining Your Bank Account
Malware attacks can lead to significant financial losses. Cybercriminals may use stolen credit card information to make unauthorized Free Downloads, or they may trick users into sending money to fraudulent accounts.
3. Identity Fraud: Impersonating You for Malicious Gain

Stolen personal information can be used for identity fraud, where criminals impersonate you to open new accounts, obtain loans, or commit other crimes in your name.
4. Device Compromise: Rendering Your Device Useless

Some malware attacks can completely compromise your mobile device, rendering it unusable. This can result in the loss of important data, disruption of communication, and inconvenience.
Essential Measures to Defend Against Mobile Malware Attacks
1. Practice Vigilance and Awareness

One of the most important steps you can take to protect your mobile device from malware is to practice vigilance and awareness. This includes being cautious of suspicious emails and text messages, avoiding downloading apps from untrusted sources, and keeping your operating system and apps up to date.
2. Use a Mobile Security Solution
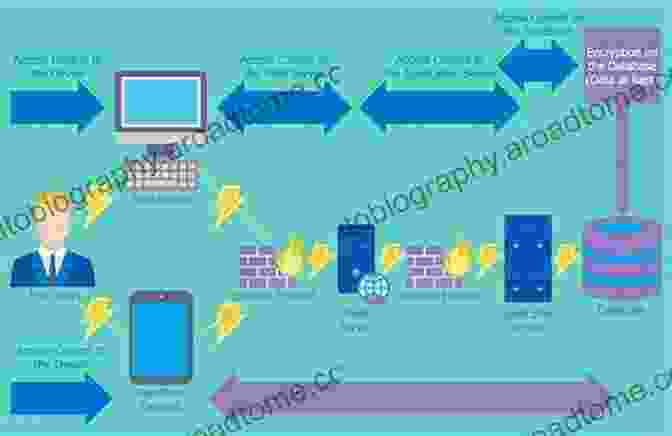
A mobile security solution can provide comprehensive protection against malware attacks. These solutions typically include features such as malware detection and removal, phishing protection, and app scanning.
3. Enable Two-Factor Authentication
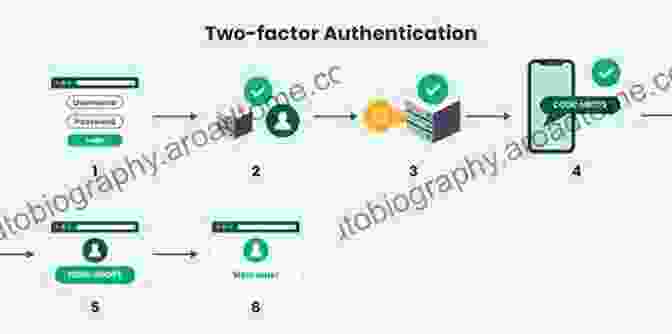
Two-factor authentication adds an extra layer of security to your accounts by requiring you to provide two forms of identification when you log in. This makes it much more difficult for cybercriminals to access your accounts, even if they have your password.
4. Keep Your Operating System and Apps Updated
Software updates often include security patches that fix vulnerabilities that could be exploited by malware. By keeping your operating system and apps up to date, you can reduce the risk of your device being infected by malware.
5. Back Up Your Data Regularly

In the event of a malware attack, backing up your data regularly can help you recover your important files and information. There are various ways to back up your data, such as using cloud storage services or connecting your device to a computer.
: Safeguarding Your Mobile Devices in the Digital Age
In the ever-evolving digital landscape, mobile malware attacks pose a significant threat to our privacy, security, and financial well-being. By understanding the sinister techniques of malware, its devastating consequences, and the crucial measures we can take to defend against it, we can effectively safeguard our mobile devices and protect ourselves from the malicious intentions of cybercriminals.
Remember, vigilance, awareness, and proactive protection are essential in the battle against mobile malware. By following the recommendations outlined in this article, you can significantly reduce the risk of your device being compromised and keep your data and privacy secure.
Stay informed, stay vigilant, and protect your mobile devices from the ever-present threat of malware.
4.7 out of 5
| Language | : | English |
| File size | : | 5625 KB |
| Text-to-Speech | : | Enabled |
| Enhanced typesetting | : | Enabled |
| Print length | : | 666 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Ayatullah Murtadha Mutahhari
Ayatullah Murtadha Mutahhari Lj Andrews
Lj Andrews Rittik Chandra
Rittik Chandra Zoran Nikolic
Zoran Nikolic Peter Oluwole
Peter Oluwole Ashfaque Ahmed
Ashfaque Ahmed Janie Marie
Janie Marie Jason Pawloski
Jason Pawloski Ronnie Cummins
Ronnie Cummins Karen Greenvang
Karen Greenvang Parva Zarei
Parva Zarei Sue Lilly
Sue Lilly 6th Edition Kindle Edition
6th Edition Kindle Edition Arif Jmsh
Arif Jmsh Carissa Gustafson Psyd
Carissa Gustafson Psyd Pam Houston
Pam Houston Raihan Kadri
Raihan Kadri John J Robinson
John J Robinson Karen Emilson
Karen Emilson Kaya Bromley
Kaya Bromley
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Clarence MitchellArchitectural Styles Visual Guide: Your Essential Companion to Understanding...
Clarence MitchellArchitectural Styles Visual Guide: Your Essential Companion to Understanding... Darnell MitchellFollow ·2.8k
Darnell MitchellFollow ·2.8k Gabriel MistralFollow ·8.7k
Gabriel MistralFollow ·8.7k Mitch FosterFollow ·7.5k
Mitch FosterFollow ·7.5k Carter HayesFollow ·3.3k
Carter HayesFollow ·3.3k Henry David ThoreauFollow ·7.9k
Henry David ThoreauFollow ·7.9k Stephen KingFollow ·14.5k
Stephen KingFollow ·14.5k Jace MitchellFollow ·15k
Jace MitchellFollow ·15k Gene SimmonsFollow ·19.2k
Gene SimmonsFollow ·19.2k

 Nathan Reed
Nathan ReedProgress In Complex Systems Optimization Operations...
This book presents...

 Duncan Cox
Duncan CoxHSK Chinese Grammar: The Ultimate Guide to Master Chinese...
HSK Chinese...

 Owen Simmons
Owen SimmonsDevelopment and Applications in Policy Support...
Unveiling the Transformative...

 Travis Foster
Travis FosterTransform Emotions Into Energy To Achieve Your Greatest...
Do you feel like your...

 Joe Simmons
Joe SimmonsUnlocking the Frontiers of Artificial Intelligence: Delve...
In the annals of artificial...
4.7 out of 5
| Language | : | English |
| File size | : | 5625 KB |
| Text-to-Speech | : | Enabled |
| Enhanced typesetting | : | Enabled |
| Print length | : | 666 pages |