Challenges and Solutions Series in Security, Privacy, and Trust

In the burgeoning digital landscape, ensuring the security, privacy, and trust of our online interactions has become paramount. However, this realm is fraught with intricate challenges that demand innovative solutions. Our comprehensive series, "Challenges and Solutions in Security, Privacy, and Trust," delves into the depths of these challenges, providing a roadmap to safeguard your digital assets, protect sensitive information, and foster confidence in the online world.
Chapter 1: The Evolving Cybersecurity Landscape
As technology advances at an unprecedented pace, so too do the threats to our cybersecurity. This chapter examines the ever-evolving nature of cyber threats, ranging from phishing scams to sophisticated malware attacks. We delve into the strategies employed by malicious actors and explore the measures organizations and individuals can take to stay ahead of the curve.
Key Takeaways:
* Understanding the latest cybersecurity trends and vulnerabilities * Implementing robust security measures to protect networks and systems * Adopting proactive approaches to threat detection and prevention
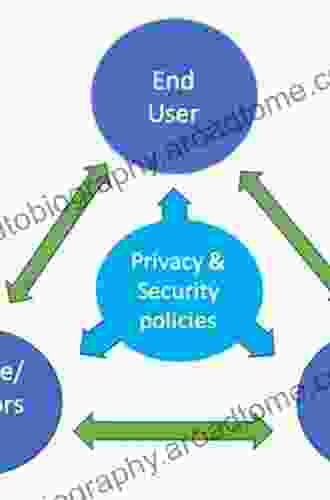
Chapter 2: The Privacy Paradox: Balancing Convenience and Security
In the pursuit of seamless online experiences, we often surrender our personal data without fully understanding the implications. This chapter investigates the privacy paradox, where individuals prioritize convenience over privacy concerns. We examine the ethical and legal considerations surrounding data collection and usage, empowering readers to make informed decisions about safeguarding their privacy.
Key Takeaways:
* Navigating the complex landscape of privacy laws and regulations * Understanding the risks associated with sharing personal information online * Developing strategies to protect privacy without compromising convenience
Chapter 3: Building Trust in the Digital Age
Trust is the bedrock of any successful online interaction. This chapter explores the challenges in establishing and maintaining trust in the digital realm. We delve into the factors that influence trust, including reputation, transparency, and security. Readers will learn how to build and sustain trust with customers, partners, and stakeholders in the increasingly interconnected online world.
Key Takeaways:
* Identifying the key elements that foster trust online * Developing strategies to enhance reputation and credibility * Implementing measures to demonstrate transparency and accountability
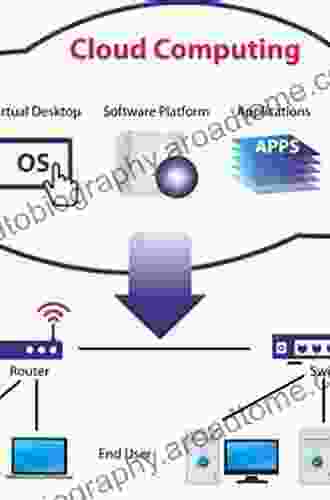
Chapter 4: Emerging Technologies and their Impact on Security, Privacy, and Trust
From blockchain and artificial intelligence to the Internet of Things, emerging technologies are transforming the way we live, work, and interact online. This chapter examines the potential benefits and challenges these technologies present for security, privacy, and trust. We explore the need for tailored strategies to mitigate risks and harness the power of emerging technologies responsibly.
Key Takeaways:
* Understanding the security and privacy implications of emerging technologies * Developing frameworks for ethical and responsible use of new technologies * Preparing for the future of technology and its impact on our digital lives
Chapter 5: The Future of Security, Privacy, and Trust
As the digital landscape continues to evolve, so too must our approaches to security, privacy, and trust. This concluding chapter provides insights into the future of these critical areas. We explore the role of regulation, innovation, and social responsibility in shaping the digital landscape of tomorrow. Readers will gain a comprehensive understanding of the challenges and opportunities that lie ahead.
Key Takeaways:
* Anticipating and preparing for future threats to security, privacy, and trust * Identifying emerging trends and solutions to address evolving challenges * Fostering a culture of collaboration and innovation to build a more secure, private, and trustworthy online world
Our "Challenges and Solutions in Security, Privacy, and Trust" series serves as an invaluable resource for individuals and organizations seeking to navigate the intricate challenges of the digital age. By understanding the latest threats and trends, embracing proactive strategies, and fostering a culture of trust, we can safeguard our digital assets, protect our privacy, and build a foundation of confidence in the online world.
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Thea Esperanza Amidov
Thea Esperanza Amidov Bruce Fink
Bruce Fink Diana Fosha
Diana Fosha Harvey H Jackson
Harvey H Jackson Erik Hanberg
Erik Hanberg Marcy Blum
Marcy Blum William Joyce
William Joyce Dan O Brien
Dan O Brien David Boyd
David Boyd Martin Luther King Jr
Martin Luther King Jr Alex Gomes
Alex Gomes Kevin B Hull
Kevin B Hull Charles Sabo
Charles Sabo Pam Houston
Pam Houston Jaecheol Koh
Jaecheol Koh Andrea Marsh
Andrea Marsh Danny Schechter
Danny Schechter Charles G Roland
Charles G Roland Rev Exp Edition Kindle Edition
Rev Exp Edition Kindle Edition Steve Coll
Steve Coll
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Reed MitchellEnvironment 10th Edition: A Comprehensive Guide to Environmental Science by...
Reed MitchellEnvironment 10th Edition: A Comprehensive Guide to Environmental Science by... Barry BryantFollow ·16.5k
Barry BryantFollow ·16.5k Marcus BellFollow ·19k
Marcus BellFollow ·19k Shaun NelsonFollow ·19.5k
Shaun NelsonFollow ·19.5k Allen GinsbergFollow ·9.8k
Allen GinsbergFollow ·9.8k Herbert CoxFollow ·11.8k
Herbert CoxFollow ·11.8k Javier BellFollow ·6.5k
Javier BellFollow ·6.5k W.B. YeatsFollow ·14.8k
W.B. YeatsFollow ·14.8k Stephen FosterFollow ·4.8k
Stephen FosterFollow ·4.8k

 Nathan Reed
Nathan ReedProgress In Complex Systems Optimization Operations...
This book presents...

 Duncan Cox
Duncan CoxHSK Chinese Grammar: The Ultimate Guide to Master Chinese...
HSK Chinese...

 Owen Simmons
Owen SimmonsDevelopment and Applications in Policy Support...
Unveiling the Transformative...

 Travis Foster
Travis FosterTransform Emotions Into Energy To Achieve Your Greatest...
Do you feel like your...

 Joe Simmons
Joe SimmonsUnlocking the Frontiers of Artificial Intelligence: Delve...
In the annals of artificial...