Mastering Security with Security Patterns In Practice

A Comprehensive Guide to Implementing Effective Security Measures
4.4 out of 5
| Language | : | English |
| File size | : | 15420 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 785 pages |
| Lending | : | Enabled |
In today's interconnected world, security has become a paramount concern for organizations of all sizes. Cybersecurity threats are constantly evolving, making it crucial to adopt robust security measures to protect your systems, data, and assets. "Security Patterns In Practice" is a comprehensive guide that empowers you to implement effective security measures by leveraging proven security patterns.
What are Security Patterns?
Security patterns are well-defined, reusable solutions to common security problems. They provide a systematic approach to addressing security risks and vulnerabilities, ensuring consistency and reducing the risk of human error. By leveraging security patterns, you can save time and resources while enhancing the overall security posture of your organization.
Why Security Patterns In Practice?
"Security Patterns In Practice" is an invaluable resource for security professionals, software architects, and developers. It offers a wealth of practical guidance on how to apply security patterns in real-world scenarios. With this book, you will learn:
* How to identify and analyze common security threats and vulnerabilities * The principles and best practices of security patterns * How to select and implement appropriate security patterns for your specific needs * Common pitfalls to avoid when using security patterns * Real-world case studies and examples to illustrate the application of security patterns
Benefits of Security Patterns
Using security patterns provides numerous advantages, including:
* Reduced Risk: Security patterns mitigate known security vulnerabilities, reducing the risk of exploits and breaches. * Improved Consistency: By leveraging standardized patterns, you ensure a consistent approach to security across your organization. * Time and Cost Savings: Security patterns provide reusable solutions, saving development time and reducing maintenance costs. * Enhanced Security Posture: Adopting security patterns helps you create a more secure and resilient IT environment.
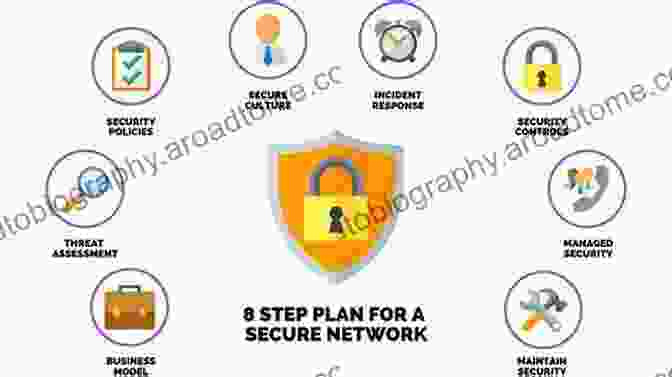
Content of Security Patterns In Practice
"Security Patterns In Practice" is structured into three parts:
Part 1: Fundamentals of Security Patterns
* Overview of security patterns * Principles and best practices * Types of security patterns
Part 2: Common Security Patterns
* Authentication and authorization patterns * Data protection patterns * Network security patterns * Application security patterns
Part 3: Applying Security Patterns
* How to select and implement security patterns * Common pitfalls to avoid * Case studies and examples
Target Audience
"Security Patterns In Practice" is ideal for:
* Security professionals * Software architects and developers * IT professionals * Compliance officers * Risk managers * Students interested in cybersecurity
"Security Patterns In Practice" is an indispensable guide for anyone seeking to enhance the security of their systems and applications. By leveraging proven security patterns, you can address common security threats and vulnerabilities, improve consistency, and reduce risks. Invest in this valuable resource and empower yourself to create a more secure and resilient IT environment for your organization.
Free Download Your Copy Today!
Visit our website to Free Download your copy of "Security Patterns In Practice" and start implementing effective security measures today.
4.4 out of 5
| Language | : | English |
| File size | : | 15420 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 785 pages |
| Lending | : | Enabled |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Glenn Nystrup M S
Glenn Nystrup M S Joseph R Dodson
Joseph R Dodson Caroline Myss
Caroline Myss Linda Richard
Linda Richard Emma Moore
Emma Moore Pam Houston
Pam Houston Rebecca Solnit
Rebecca Solnit Estela Mara Bensimon
Estela Mara Bensimon Jess French
Jess French Anne Ake
Anne Ake Rick Young
Rick Young Antony Cummins
Antony Cummins Mary Holland
Mary Holland Richard Busulwa
Richard Busulwa Robert Kaluza
Robert Kaluza Sydney Foster
Sydney Foster Dov Davidoff
Dov Davidoff Zack Arias
Zack Arias Eliane Kurbegov
Eliane Kurbegov Gitika Commuri
Gitika Commuri
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Samuel Taylor ColeridgeAsk In Prayer: Unlocking the Extraordinary Power of Prayer with Tom Bowers
Samuel Taylor ColeridgeAsk In Prayer: Unlocking the Extraordinary Power of Prayer with Tom Bowers
 Clarence MitchellPhytochemicals In Health And Disease: Unveiling the Power of Nature's Defense
Clarence MitchellPhytochemicals In Health And Disease: Unveiling the Power of Nature's Defense Bryson HayesFollow ·18.6k
Bryson HayesFollow ·18.6k Rick NelsonFollow ·12.8k
Rick NelsonFollow ·12.8k Dave SimmonsFollow ·13k
Dave SimmonsFollow ·13k Curtis StewartFollow ·4.1k
Curtis StewartFollow ·4.1k Forrest BlairFollow ·18.2k
Forrest BlairFollow ·18.2k Forrest ReedFollow ·4.9k
Forrest ReedFollow ·4.9k Eugene PowellFollow ·19.4k
Eugene PowellFollow ·19.4k Leslie CarterFollow ·11.7k
Leslie CarterFollow ·11.7k

 Nathan Reed
Nathan ReedProgress In Complex Systems Optimization Operations...
This book presents...

 Duncan Cox
Duncan CoxHSK Chinese Grammar: The Ultimate Guide to Master Chinese...
HSK Chinese...

 Owen Simmons
Owen SimmonsDevelopment and Applications in Policy Support...
Unveiling the Transformative...

 Travis Foster
Travis FosterTransform Emotions Into Energy To Achieve Your Greatest...
Do you feel like your...

 Joe Simmons
Joe SimmonsUnlocking the Frontiers of Artificial Intelligence: Delve...
In the annals of artificial...
4.4 out of 5
| Language | : | English |
| File size | : | 15420 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 785 pages |
| Lending | : | Enabled |